2-Factor Authentication FAQs
What is 2FA? Why is Muhlenberg requiring the use of Two-Factor Authentication?
Also known as Multi-factor or Dual Factor Authentication, this technology requests a second form of verification when logging into an account. The key part is that the phone or hardware token is likely to be in your physical possession. Someone else might have your password (via a successful phishing scam, for instance), but they won’t likely have your phone, too, or that hardware token. Obviously, if you get an alert when you haven’t been trying to log in, go right away and change your password, too. But it’s good to know that an unauthorized user can’t get in without that second factor.
I heard other institutions only 2FA specific applications, like financial ones. Why are we 2FA’ing the entire Application Portal?
We are adding 2-Factor Authentication to the Application Portal to immediately protect you for your G Suite (Gmail, Drive, etc), Workday activities, the Canvas LMS and a number of other services all in one fell swoop. We consider your email just as important as your Workday activities, for instance. As we continue to add applications to the portal, it is critical to safeguard your account.
How do I set up 2-Factor Authentication?
You may set up 2-Factor Authentication on any mobile device on which you can install the OneLogin Protect app and/or Google Authenticator.
For step-by-step instructions, visit 2-Factor Authentication for documentation and tutorials.
If you do not have a smartphone or tablet, SMS (text messaging) is a 2-Factor option. A hardware token called a Yubikey may be requested for faculty and staff. Students may purchase them independently.
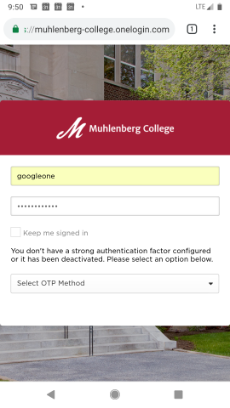
What happens if I try to login off campus and have not yet registered a factor?
The screenshot below displays what you will see, including the message "You don't have a strong authentication factor configured or it has been deactivated. Please select an option below."
You must "Select an OTP (one time password) Method" and register a factor in order to have access to the application portal when off campus. You may set up 2-Factor Authentication on any mobile device on which you can install the OneLogin Protect app and/or Google Authenticator. For step-by-step instructions, visit 2-Factor Authentication for documentation and tutorials.
How will my mobile device be affected by the OneLogin app (Google Authenticator etc..)?
Other than the installation of the apps, it should not affect performance or battery usage in any significant way.
What do I do if my smartphone is broken or lost/stolen?
If your smartphone is lost/stolen or broken, contact the Support Desk immediately at 484-664-3566. Upon verifying your identity, the Support Desk will generate a one time passcode for your account. Once you have access, you will need to revoke the existing factors on your account. We will issue a Yubikey on loan until you obtain a new device.
What should I do if I receive an unexpected notification from OneLogin to authenticate?
This means that someone else with your password is trying to access your account. Any unexpected notification to verify access to your account should be denied. You will want to change your Muhlenberg network password immediately. Next step, contact the Support Desk to report this occurrence and we will open an incident to look into this suspicious activity.
I’m going to be traveling soon. Will everything still work?
As long as you have installed the OneLogin Protect and/or Google Authenticator app on your device and registered your factor(s) your second factor(s) in the portal, you will be ready for access from any location.
Can I get the 2nd factor via text message?
OneLogin Mobile SMS is available to use as a second factor. Setting up an SMS is not as secure as using the OneLogin Protect App or Google Authenticator; we only recommend using this if your phone cannot support running the application due to an older OS or lack of memory.
You will need to add your mobile number to your OneLogin application portal profile first. After doing so, you register your mobile device for 2-Factor Authentication by selecting OneLogin SMS as a device. You will be sent a verification code via text to confirm this factor. Please note, charges may apply depending on your wireless plan. This is a standard text message.
See Setting up SMS as 2nd Factor for step-by-step instructions.
Do I need internet or cell service to use 2FA?
In order to login with 2FA, you do not need internet or cell service. Simply go into the OneLogin Protect App, or Google Authenticator, and use the six digit passcode to enter into the application portal. When you are logging in, be sure to press on the “enter passcode” button to input the 6 digit code. Similarly, the hardware token does not need internet access; follow the directions here.
What do I do if I want to change phones?
Ideally, you will want to install the app and register your second factor(s) on the new device, before revoking the factors previously registered on the outgoing device.
What do I do if I don’t have a smartphone or tablet?
OneLogin Mobile SMS is available to use as a second factor. See Setting up SMS as 2nd Factor for step-by-step instructions.
Faculty and staff can request a hardware token using the 2-factor hardware token request form.
How do I get a YubiKey token?
Faculty and staff can request a hardware token using the 2-factor hardware token request form. Please note that there are criteria to qualify for a token.
What happens if I lose my YubiKey?
We have a limited amount of Yubikeys for allocation to faculty and staff based on a certain set of criteria. The first one is on us. The cost to replace a Yubikey is $40.
When I plug in my YubiKey the light does not turn on. What do I do?
You may have the Yubikey inserted incorrectly into your computer. See Registering and Using a Yubikey for 2-Factor to learn more.
